Sign commits with a GPG key using a passphrase with pinentry-mac
With the increasing prevalence of inserting malicious code into commonly-used open source projects on the rise, it might be time to enforce commit signing for your open source project. This prevents someone from spoofing your identity on commits they make. If it’s not signed with your key, then it’s not verified and the UI will show this.
When setting up gpg (v2) to automatically sign your commit messages, you may run into an error:
error: gpg failed to sign the data
fatal: failed to write commit object
If you re-run your git commit command with GIT_TRACE=1, you can see it
running gpg --status-fd=2 -bsau <your-signing-key> but failing.
The cause of this is the pinentry process. By default gpg uses the
pinentry program which requires a TTY and access to the shell’s stdin.
This doesn’t appear to function properly on a Mac. Instead, you should use
pinentry-mac.
$ brew install pinentry-mac
$ echo "pinentry-program /usr/local/bin/pinentry-mac" >> ~/.gnupg/gpg-agent.conf
$ gpgconf --kill gpg-agent
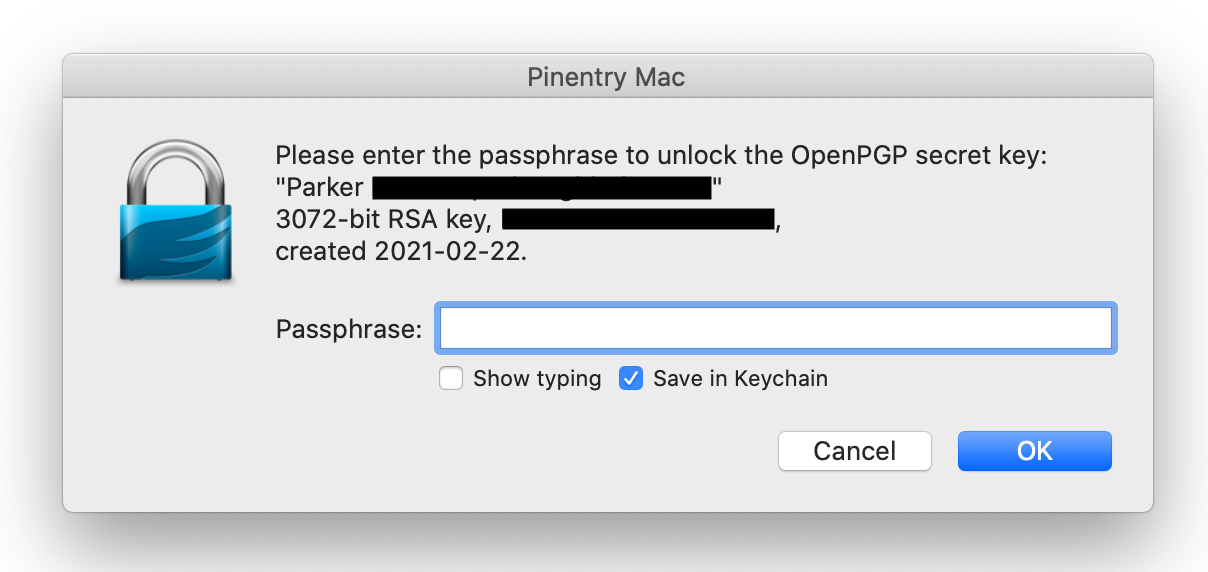
Re-run your git commit command and you should see a GUI pop-up to request
your GPG key’s passphrase. Enter it and the commit will succeed!
You can setup automatic signing with the following commands:
$ git config --global user.signingkey <key_id>
$ git config --global commit.sign true
$ git config --global commit.gpgSign true
Make sure to upload your GPG key to your GitHub account:
$ gpg --armor --export <key_id>
Happy signing!